aws iam in 30 seconds
2020-05-27
|~3 min read
|405 words
Preamble: I am exploring different areas of AWS and am finding the jargon overwhelming. To help myself, I’ll be writing up summaries of some of the different services I come across, what they are, some core concepts, and links to resources for future reference.
All entries in the series are tagged with
aws in 30 secondsand can be found here.
Introduction to AWS Identity and Access Management | AWS Training
High level: Identity & Access Management (IAM) is a service provided by AWS to manage individual and group access to AWS resources. This is accomplished by authenticating and authorizing users based on IAM users, roles and/or groups.
Authentication
There are three different ways that a user can authenticate (a prerequisite to accessing any AWS resources):
- AWS CLI
- AWS SDKs
- AWS Management Console.
Authorization
By default, all resources are private to a user’s account. To grant permissions IAM users and groups must be granted access via IAM policies.
Policies
An IAM Policy is a JSON document that records the effects, actions, resources and optional conditions for what API calls a policy holder may invoke.
Anything not explicitly listed is not permitted. Here’s a sample policy:
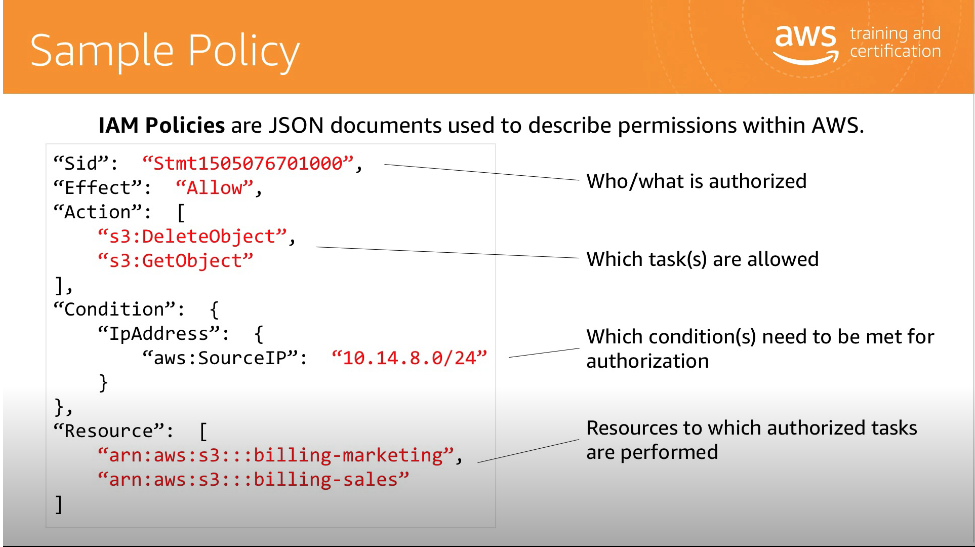
Roles
In addition to Groups, Policies, and Users, there are also IAM Roles.
Roles are similar to Users in that they can be used to determine which resources are accessible, however they are not uniquely associated with an individual and they have no standard login credentials.
They are used to delegate access to a user temporarily. When a user assumes a role, they give up their own permissions and take on the permissions of the role.
Utilizing IAM Roles avoids the need to modify a specific user’s permissions each time a change is required.
Wrap Up
Putting this into practice. Imagine setting up the permissions for an organization.
- Create an IAM Group or groups
- Create IAM Policy (or policies) and assign them to the group(s)
- Create IAM Users for each individual and assign them to their respective IAM Group In this way, user permissions are efficiently managed.
If a user only needs temporary access to certain resources, IAM Roles are a good bet. They are also helpful in avoiding embedding credentials directly into an application.
Resources
Hi there and thanks for reading! My name's Stephen. I live in Chicago with my wife, Kate, and dog, Finn. Want more? See about and get in touch!